Overview#
OpenID Connect (OIDC) is an interoperable Authentication Protocol based on the OAuth 2.0 family of specifications provided by the OpenID FoundationOpenID Connect uses straightforward REST/JSON message flows with a design goal of "making simple things simple and complicated things possible".
OpenID Connect is uniquely easy for developers to integrate, compared to any preceding Identity protocol.
OpenID Connect lets developers authenticate their users across websites and apps without having to own and manage password files. For the app builder, OpenID Connect provides a secure verifiable, answer to the question "What is the identity of the person currently using the browser or native app that is connected to me?"
OpenID Connect allows for clients of all types, including browser-based JavaScript and native mobile apps, to launch sign-in flows and receive verifiable assertions about the identity of signed-in users.
OpenID Connect is ideally suited for WEB Access Management.
OpenID Connect is an standard that profiles and extends OAuth 2.0 to add an identity layer – creating a single framework that promises to secure APIs, mobile native applications, and browser applications in a single, cohesive architecture.
OpenID Connect Identity#
OpenID Connect adds two notable identity constructs to OAuth 2.0's token issuance model.- an Identity Token - the delivery of which from one party to another can enable a Federated Identity SSO user experience
- a standardized identity attribute API - at which a client can retrieve desired identity attributes for a given user.
OpenID Connect provides the Relying Party answers to these Questions:#
- Who is the Digital Identity that performed the Authentication
- Where did the Authentication take place (ie What Identity Provider (IDP)
- When was the Digital Identity Authentication process.
- How was the Digital Identity Authentication performed
- What Digital Identity Attributes are available to you
- Why did the Digital Identity provide access to the attributes
OpenID Connect Libraries#
OpenID Connect (OpenID Connect Core 1.0) Specification is 86 pages of technical jargon not counting the many extensions and references. Not using OpenID Connect libraries and trying to roll your own is not correct thinking. Use the OpenID Connect Client libraries or a "Known Good" implementation created by experts.Relationship to OAuth 2.0#
OpenID Connect provides identity semantics and constructs on top of OAuth 2.0 by logically adding layers onto the OAuth 2.0 base as opposed to other non-identity centric applications that are possible with OAuth 2.0.The OpenID Connect specification uses the terms:
- Access Token
- Authorization Code
- Authorization_endpoint
- Authorization Grant
- Authorization Server
- Client
- Client_id
- Client Secret
- Grant Type
- Protected Resource
- Redirect_uri
- Refresh Token
- Resource Owner
- Resource Server
- Response_type
- Token_endpoint
OpenID Connect terms:
as defined by JSON Web Token (JWT)OpenID Connect terms as defined by JSON Web Signature (JWS)
OpenID Connect term User-agent defined by RFC 2616
OpenID Connect term Response_mode defined by OAuth 2.0 Multiple Response Type Encoding Practices
OpenID Connect introduces notable identity constructs on top of the OAuth 2.0 base protocol:
- Defined OAuth Scopes - OpenID, Profile, email, address, phone
- Identity Token
- UserInfo Endpoint
- Openid-configuration Endpoint - Makes available configuration information that describes the Connect Authorization Server.
OpenID Connect Leverages other emerging technologies
- Allows choice of Identity Provider (IDP)
- REST/JSON Friendly:
- Can provide Level Of Assurance
- Implements User Managed Access
Set to be adopted by Facebook, Google, and others
OpenID Connect Flows#
There are several OpenID Connect FlowsThis is a General Diagram of OpenID Connect Flows:
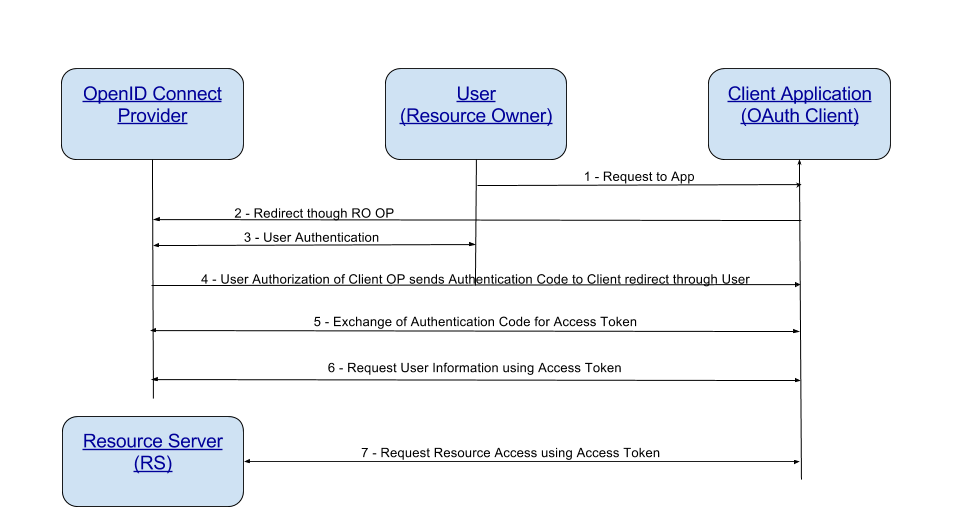 |
OpenID Connect Endpoints#
OpenID Connect Documents#
- OpenID Connect Core 1.0 incorporating errata set 1

- OpenID Connect Discovery 1.0 incorporating errata set 1

- OpenID Connect Dynamic Client Registration 1.0 incorporating errata set 1

- OpenID Connect Basic Client Implementer's Guide 1.0

- OpenID Connect Implicit Client Implementer's Guide 1.0

- OpenID Provider Authentication Policy Extension 1.0

- OpenID Connect Session Management 1.0

- OpenID Connect for Identity Assurance
More Information#
There might be more information for this subject on one of the following:- API-Gateway
- AWS Cognito
- Access Proxy
- Access Token
- Access Token Validation
- Account_selection_required
- Acr
- App2app
- AppAuth
- Auth 2.0 Resource Set Registration
- Authentication Context Class
- Authentication Context Class Reference
- Authentication Double-Hop
- Authentication Method
- Authentication Method Reference
- Authentication Protocol
- Authentication Request
- Authorization Code Flow
- Authorization Cross Domain Code 1.0
- Authorization Request
- Authorization Request Parameters
- Authorization Server
- Authorization Server Authentication of the End-User
- Authorization Server Request End-User Consent-Authorization
- Authorization_endpoint
- Best Practices OpenID Connect
- Best Practices Password
- Best Practices for LDAP Security
- Claim
- Claim_types_supported
- Claims_locales
- Claims_parameter_supported
- Claims_supported
- Client Authentication Methods
- Client Secret
- Consent Dialog
- Consent Standards
- Consent_required
- Cool Identity Token Uses
- Covert Redirect Vulnerability
- Curity
- DID Authentication
- Digital Identity
- Display Parameter
- Display_values_supported
- Essential Claim
- FAL 1
- FAL 2
- FAPI Pushed Request Object
- Fast Healthcare Interoperability Resources
- Federated Credential
- Federated Identity
- Federation Assurance Level
- Frontchannel_logout_session_required
- Frontchannel_logout_uri
- Grant
- Grant Negotiation and Authorization Protocol
- Grant Types
- Grant_types_supported
- Health Relationship Trust
- Hosted domain
- Hybrid Flow
- Id_token_encryption_alg_values_supported
- Id_token_encryption_enc_values_supported
- Id_token_signing_alg_values_supported
- Identity Broker
- Identity Provider (IDP)
- Identity Token
- Identity Token Claims
- Identity Toolkit ID Token
- IdentityServer
- Interaction_required
- Invalid_request_object
- Invalid_request_uri
- Iss
- Issuer
- JSON Identity Suite
- JSON Web Token Best Current Practices
- JWK Set
- Javascript Object Signing and Encryption
- Jwks_uri
- Kerberos
- Level of Assurance (LoA) Profiles
- Level of Identity Proofing
- Life Management Platform
- Login_required
- Logout Mechanism
- Lua-resty-openidc
- MITRE Corporation
- MITREid Connect
- Malicious Endpoint
- Max_age
- Mix-up attacks
- Mobile Connect
- Mobile Operator Discovery, Registration & Authentication
- Native Applications Working Group
- Neo-Security Stack
- OAuth 2.0 Authorization
- OAuth 2.0 Client Registration
- OAuth 2.0 Dynamic Client Registration Protocol
- OAuth 2.0 JWT Secured Authorization Request
- OAuth 2.0 NOT an Authentication protocol
- OAuth 2.0 Protocol Flows
- OAuth 2.0 Security Best Current Practice
- OAuth 2.0 Security Considerations
- OAuth 2.0 Token Exchange Request
- OAuth 2.0 Vulnerabilities
- OAuth Client
- OAuth Dynamic Client Registration Metadata
- OAuth Parameters Registry
- OAuth Scope Example
- OAuth Scopes
- OAuth Token Response
- OAuth and OIDC Adoption
- OIDC
- OIDC SSO
- OXD
- Offline_access
- Oidc-client-js
- Op_policy_uri
- Op_tos_uri
- Open Banking
- Open Banking Implementation Entity
- Open Banking OBIE
- Open Trust Taxonomy for OAuth2
- Open Web Interface for .NET
- OpenAM Endpoints
- OpenID
- OpenID Artifact Binding Working Group
- OpenID Connect Account Porting
- OpenID Connect Certified
- OpenID Connect Claims
- OpenID Connect Client Initiated Backchannel Authentication Flow
- OpenID Connect Core 1.0
- OpenID Connect Discovery
- OpenID Connect Dynamic Client Registration
- OpenID Connect Endpoints
- OpenID Connect Federation
- OpenID Connect Federation Async
- OpenID Connect Flows
- OpenID Connect MODRNA Authentication Profile 1.0
- OpenID Connect Profile for SCIM Services
- OpenID Connect Profiles
- OpenID Connect Provider
- OpenID Connect Scopes
- OpenID Connect Session Management
- OpenID Connect Standard Claims
- OpenID Connect Use Cases
- OpenID Connect for Identity Assurance
- OpenID Provider Issuer Discovery
- OpenID.Registration
- OpenPDS
- Openid scope
- Openid-configuration
- OxAuth
- Ping Identity
- Privacy Enhancing Technologies
- Prompt Parameter
- Proof Key for Code Exchange by OAuth Public Clients
- Proof-of-Possession Key Semantics for JSON Web Tokens (JWTs)
- REST Profile of XACML
- Refresh Token
- Registration_not_supported
- Relying Party
- Remember Me
- Representational State Transfer
- Request_not_supported
- Request_object_encryption_alg_values_supported
- Request_object_encryption_enc_values_supported
- Request_object_signing_alg_values_supported
- Request_parameter_supported
- Request_uri
- Request_uri_not_supported
- Require_request_uri_registration
- Resource Owner
- Resource Server
- Response_modes_supported
- Response_types_supported
- Revocation_endpoint
- Salesforce
- Scopes vs Claims
- Self-Issued OpenID Provider
- Service_documentation
- Session Management
- Single Sign-On Scenarios
- Smart-On-FHIR profile
- Social Login
- Standards Based SSO
- Sub
- Subject_types_supported
- The Next Big Thing
- Token Binding over HTTP
- Token_endpoint
- Token_endpoint_auth_methods_supported
- Two-Factor Authentication
- Ui_locales
- User-Managed Access
- UserInfo Request
- UserInfo Response
- Userinfo_endpoint
- Vector of Trust Request
- Verified_claims
- Voluntary Claim
- WEB Access Management
- Web Authentication
- WebFinger
- What To Do About Passwords
- What is missing in OAuth 2.0
- Why OAuth 2.0
- Why OpenID Connect
- Windows Hello
- Yadis
- [#1] - OpenID Connect
 - based on 2015-05-14
- based on 2015-05-14
- [#2] - OpenID Connect 1.0 for Enterprise
 - based on 2015-05-14
- based on 2015-05-14