Overview#
The Full TLS Handshake is what is shown in How SSL-TLS Works.The TLS Full Handshake looks like this:
Client Server
ClientHello -------->
ServerHello
Certificate*
ServerKeyExchange*
CertificateRequest*
<-------- ServerHelloDone
Certificate*
ClientKeyExchange
CertificateVerify*
[Change_cipher_spec]
Finished -------->
[Change_cipher_spec]
<-------- Finished
Application Data <-------> Application Data
TLS 1.3 TLS Full Handshake[1]#
As RSA key-exchange is no longer supported in TLS 1.3 means we can start with TLS Full Handshake using Perfect Forward Secrecy using Diffie-Hellman.Another important change is the removal of the Change_cipher_spec protocol. With TLS 1.3 every message sent after ServerHello is encrypted with the so-called Ephemeral Key secret to lock out passive Passive attackers.
EncryptedExtensions carries Hello extension data that must be encrypted because it is not needed to set up secure connection.
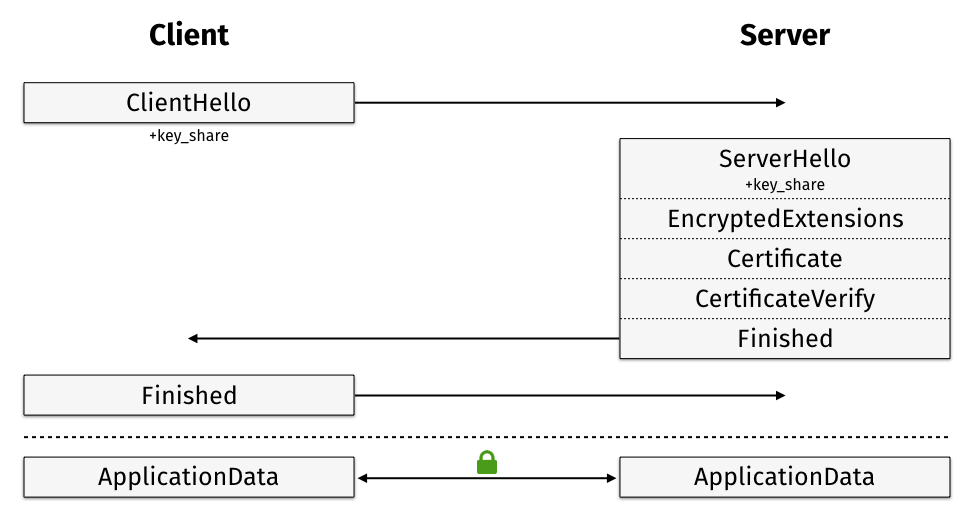 |
One of the most important change with regard to 1-RTT Handshake is the removal of the ServerKeyExchange and ClientKeyExchange messages.
The DH parameters and Public Keys are now sent in special KeyShare extensions, a new type of extension to be included in the ServerHello and ClientHello messages. Moving this data into Hello extensions keeps the handshake compatible with TLS 1.2 as it doesn’t change the order of messages.
The client sends a list of KeyShareEntry values, each consisting of a named ECDH group and an Ephemeral Public Key. If the server accepts Ephemeral Public Key must respond with one of the proposed ECDH group and its own Ephemeral Public Key.
If the server does not support any of the given key shares the server will request retrying the TLS Full Handshake or abort the connection with a fatal handshake_failure alert.
More Information#
There might be more information for this subject on one of the following:- Certificate_list
- Digital certificate request
- How SSL-TLS Works
- Mutual Authentication
- ServerCertificate
- TLS Client Authentication
- TLS Handshake
- TLS Session Resumption
- [#1] - Improved Handshakes in TLS version 1.3
 - based on information obtained 2017-01-05
- based on information obtained 2017-01-05