Overview#
Authentication (AuthN) is the process of establishing to a specified Level Of Assurance that the Identification is authentic.Authentication for most of our purposes is the process a Digital Identity (Peggy) making an Assertion of Claims to a Verifier (Victor) which uses Authentication Methods to provide a Level Of Assurance by validation of the Claims.
Authentication includes Identification and is REQUIRED before you can perform Authorization.
Authentication is the function of confirming the legitimacy of a Claimant (i.e., that the Claimant is indeed the Subject which it claims to be).
Authentication is a Facet Of Building Trust.
Alice And Bob User Story#
This is a User Story where Alice wants to send Bob a message and Eve is eavesdropping in the Communication.Eve could change the message in some way. This requires Eve to have a bit more control over the communication channel, but that is not at all an impossibility.
Alice tries to send the message m, but Eve interferes with the communication channel and instead of receiving m, Bob receives a different message
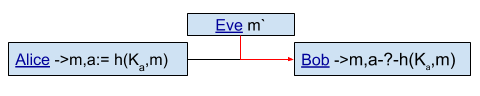 |
Where:
- m = message in Plaintext
- h = the MAC function
- Ka = Authentication Key (requires Key-Exchange)
- a = the Message Authentication Code and calculated by h(Ka, m)
When Alice sends the message, she computes the Message Authentication Code and sends both the message and the a authentication code, or MAC. When Bob receives the message and a (Message Authentication Code), Bob calculates a (Message Authentication Code) and compares to the value of a that Alice sent. Bob will recognize that the message is not correct.
Authentication is only a partial solution. Eve can still delete messages that Alice sends. Eve can also repeat old messages or change the message order.
Authentication Process#
Authentication process consists of two basic steps: (RFC 4949)- Identification step: Presenting the Assertion Value of a claim (e.g., a user identifier) to the Authentication subsystem.
- Verification step: Presenting or generating Credential (e.g., password or a value signed with a Private Key) that acts as evidence to prove the binding between the attribute and that for which it is claimed.
Authentication Classes#
- Entity Authentication - Most people relate Authentication to Entity Authentication
- Message Authentication
Authentication in the context of Identity and Access Management, this includes:
- Document verification: checking that data is correct and valid by corroboration or source verification; checking that any document security features are intact; searching for duplicates. Often used in Enrollment and Verification processes.
- Credential Authentication: can include
- a form of document verification where the credential is a controlled document issued by an authority; or
- a form of user login where a credential and authenticator are used to prove that the credential is presented and controlled by the true owner.
- Entity Authentication is a form of login using credentials and authenticators. This form deliberately avoids specification of Natural Person entities versus Non-person entity.
- Federated Authentication: Entity Authentication where the Identity Provider (IDP) is remote or separate from the resource being requested and the verifier and Relying Party use the same Authentication Method and Level Of Assurance. The Authentication verifier communicates, or asserts, the result of the Authentication to the Relying Party.
These contexts and usages have similar operations: presentation of evidence, sometimes known as ‘authenticators’ to a verifier; verification of the evidence either as-presented or against a data repository; optional corroboration of data related to the evidence; decision; action resulting from decision.
Authentication Definition#
Authentication[1] (from Greek αυθεντικός; real or genuine, from authentes; author) is the act of establishing or confirming something or someone as authentic."the real-time corroboration of a person's claimed digital Identity with an implied or notional level of trust." [2]
"The process of establishing confidence in the Digital Identity of users or information systems" (NIST.SP.800-63—2),
ISO 24745 - process of establishing an understood Level Of Confidence that a specific entity or claimed identity is genuine
Authentication Components#
Authentication Challenges#
There are many Authentication ChallengesVerifier#
Victor the (Verifier) is an entity that must be convinced that Peggy (the prover or Claimant) knows some Authentication Factors to some Level Of Assurance.Example#
The scenario we are most familiar with us when something or someone (a Digital Identity) presents (or claims) something. As an Example:- I am userid1
- and my password is Xyz
There are many Authentication Methods.
Authentication involves Trust#
In our modern day digital systems Authentication involves Trust that the Relying Party trusts the Identity Provider (IDP).LDAP Authentication#
Some details on LDAP AuthenticationLevel Of Assurance#
Authentication is always subject to a Level Of Assurance the the Third-party is willing to accept.More Information#
There might be more information for this subject on one of the following:- ACE-OAuth
- AES-GCM
- API Service Delivery
- API-Gateway
- AP_REQ
- AS_REQ
- About
- Access Control
- Access Proxy
- Access Token Type
- Acr
- Acr_values
- Agent
- Ambiguous Name Resolution
- Anonymous Cipher Suite
- Anonymous bind
- Apache Web Server and LDAP
- App2app
- Apple Pay
- Assertion Framework for OAuth 2.0 Client Authentication and Authorization Grants
- Assurance Level
- Attestation
- Attribute
- Audit Log
- AuthN
- AuthPassword
- Authenticate
- Authenticated
- Authenticated Encryption
- Authenticated Encryption with Associated Data
- Authenticated Protected Channel
- Authentication
- Authentication Center
- Authentication Channel
- Authentication Context Class
- Authentication Context Class Reference
- Authentication Context Class Values
- Authentication Context Class vs Authentication Method Reference
- Authentication Factor
- Authentication Method
- Authentication Method Reference
- Authentication Method Reference Values
- Authentication Protocol
- Authentication cookie
- Authentication intent
- Authentication, Authorization and Accounting (AAA) Transport Profile
- Authenticator
- Authenticator App
- Authenticator Assurance Levels
- Authenticity
- Authorization
- Authorization Code Flow
- Authorization Gesture
- Authorization Header
- Authorization Request Parameters
- Authorization Server
- Authorization Server Authentication of the End-User
- Authorization_endpoint
- Automatic Certificate Management Environment
- Basic Authentication Scheme
- Batch-Auth
- Best Practices For Unique Identifiers
- Best Practices OpenID Connect
- Best Practices for LDAP Security
- BeyondCorp
- BiDirectionalDriver
- Bind Request
- Bind Response
- Binding_message
- Biometric Comparison
- Biometric Data Challenges
- Biometric Template
- Birthday
- Block Cipher Mode
- Bob Blakley
- Boulder
- Bring Your Own Identity
- Browser-view
- CAM
- CRAM-MD5
- CRAM-MD5 SASL Mechanism
- CTAP2
- CVM
- Cached and Stored Credentials
- CachedInteractive
- Cardholder Data Environment
- Certificate
- Certificate Authority
- Certificate Validation
- Certificate-based Authentication
- Challenge-response
- Challenge-response Authentication Mechanism
- Channel Binding
- Chip Card
- Cipher Suite
- Claim
- Claimant
- Client Credentials Grant
- Client To Authenticator Protocol
- ClientKeyExchange
- Closed-Loop Authentication
- Cloud Access Security Broker
- Cloud Native
- Common Domain for Identity Provider Discovery
- Common Edirectory Bind Errors
- Computer Fraud and Abuse Act
- Configuration Files For JSPWIKI And LDAP
- Consistent Sign-On
- Covert Redirect Vulnerability
- CredSSP
- Credential
- Credential Suspension
- Credential stuffing
- Cross-domain authentication
- Cross-platform Authentication
- Cryptographic Primitive
- Cryptography Objectives
- CurveCP
- DIAMETER
- DID Authentication
- DID Document
- DIGEST-MD5
- DNS-Based Authentication of Named Entities
- DSE_AUTHENTICATE
- DSE_LOGIN_EX
- DSE_NMAS_LOG_FINISH_LOGIN_STATUS
- Data Protection
- Default_acr_values
- Delegation vs Impersonation
- Differences between LDAP 2 and 3 Protocols
- Diffie-Hellman or RSA
- Digest SSP
- Digital Identity
- Digital Signature
- DigitalSignature
- Direct Anonymous Attestation
- Display Parameter
- Distributed Computing Environment
- Domain Name System Security Extensions
- Domain-based Message Authentication, Reporting & Conformance
- DomainKeys Identified Mail
- Draft-behera-ldap-password-policy
- Dump Password Information Tool-Trouble Shooting
- Dynamic Access Control
- EAX
- EMV Terms
- EdirectoryPasswords
- Electronic Identification Authentication and trust Services
- Enc
- Encapsulating Security Payload
- Enhanced Privacy ID
- Enterprise Directory
- Entity
- Entity Authentication
- Event 4625
- Extensible Authentication Protocol
- Eyeprint ID
- FAL 3
- FIDO
- FIDO Alliance
- FIDO Authenticator
- FIDO Standards
- FIDO2
- FIPS 198-1
- Fast Healthcare Interoperability Resources
- Fast IDentity Online
- Federated Authentication
- Federation
- Federation Assurance Level
- Federation Models
- Fingerprint recognition
- Firebase
- Galois Message Authentication Code
- Galois-Counter Mode
- Generic Security Service Application Program Interface
- Geneva Framework
- Glossary Of LDAP And Directory Terminology
- Gluu Server
- Google Authenticator
- Google Cloud Functions
- Google Cloud SDK
- HTTP 407
- HTTP Authentication Framework
- HTTP Status Code
- Hard tokens
- Hardware Security Module
- How passwords are used in Windows
- IAM Charter
- IDM Related Compliance Items
- IDM The Application Developers Dilemma
- IDP
- IDSA Integration Framework
- IMA Policies
- ISO 29115
- Identification
- Identified
- Identify and Authenticate access to system components
- Identity Assurance Level
- Identity Broker
- Identity Correlation
- Identity Credential and Access Management
- Identity Document
- Identity Lifecycle Management
- Identity Mixer
- Identity Proofing
- Identity Provider (IDP)
- Identity Relationship Management
- Identity Token
- Identity Token Validation
- Impersonation-resistant
- Industry 4.0
- Information security
- Initiative for Open Authentication
- Instant Messaging
- Interactive
- Internet Key Exchange
- Internet Protocol Security
- Internet of Things
- Istio
- JSON Web Token (JWT) Profile for OAuth 2.0 Client Authentication and Authorization Grants
- JSON Web Token Claims
- JSON Web Tokens
- Java Authentication Service Provider Interface for Containers
- Java Authentication and Authorization Service
- John Bradley
- Kerberos
- Kerberos Authentication Service
- Kerberos Delegation
- Kerberos Forged Ticket
- Kerberos Pre-Authentication
- Kerberos SSP
- Kerberos Service Account
- Key Distribution Center
- Key Management
- Key-Exchange
- Keyed-Hash Message Authentication Code
- Keystore
- Knowledge-Based Authentication
- Known Cipher Suites
- LAN Manager authentication level
- LCM
- LDAP Authentication
- LDAP Signing
- LDAP and Bind Throttling
- LDAP for Linux and Unix Clients
- LOA 2
- LOA 3
- LOA 4
- Last Login Time
- LastLoginTime
- LeftMenu
- Legitimacy of Social Login
- Level Of Assurance
- Liberty Alliance
- Local Security Authority
- Lockouttime
- Logical Access Control
- Login_hint_token
- Login_required
- M-04-04 Level of Assurance (LOA)
- MS-CHAP
- Macaroons
- Maverick Research The Death of Authentication
- Meet-in-the-Middle Attack
- Messaging Layer Security
- Microsoft Account
- Mobile Driver License
- Mobile Operator Discovery, Registration & Authentication
- Mobile-Digital Wallets
- Mod_auth_openidc
- Multi-Factor Authentication
- Multiple-channel Authentication
- Mutual Authentication
- Mutual TLS Profiles for OAuth Clients
- NCP Primary Authentication Protocol
- NDS Authentication
- NDS Connection States
- NDS External References
- NIST.IR 7817
- NIST.SP.38
- NIST.SP.800-207
- NIST.SP.800-63
- NIST.SP.800-63-3
- NIST.SP.800-63A
- NIST.SP.800-63B
- NIST.SP.800-63C
- NMAS
- NMAS Result Codes
- NMAS_E_INVALID_SPM_REQUEST
- NMAS_LOGIN
- NT LAN Manager
- NT LAN Manager Vulnerabilities
- NTLM SSP
- Native application
- Ndsconfig
- Ndsconfig Parameters
- Ndstrace
- Neo-Security Stack
- NetWare
- Netlogon Remote Protocol
- Netlogon service
- Network-Auth
- NetworkCleartext
- Nevis Security Suite
- Non Permissioned System
- Non-Repudiation
- Non-interactive
- Nonce
- OAuth 2.0 Authorization
- OAuth 2.0 Dynamic Client Registration Management Protocol
- OAuth 2.0 Incremental Authorization
- OAuth 2.0 JWT Secured Authorization Request
- OAuth 2.0 Message Authentication Code (MAC) Tokens
- OAuth 2.0 Mutual TLS Client Authentication and Certificate Bound Access Tokens
- OAuth 2.0 NOT an Authentication protocol
- OAuth 2.0 Protocol Flows
- OAuth 2.0 Security Best Current Practice
- OAuth 2.0 Token Exchange Request
- OAuth 2.0 Token Introspection
- OAuth 2.0 Vulnerabilities
- OAuth 2.0 for Native Apps
- OAuth Client
- OAuth Confidential Client
- OAuth Parameters Registry
- OAuth Scope Example
- OXD
- Off-the-Record Messaging
- One-Time Password System
- One-Time password
- One-time password device tokens
- Open Banking
- Open Banking Implementation Entity
- Open Banking OBIE
- Open Trust Taxonomy for OAuth2
- Open-Loop Authentication
- OpenID
- OpenID Connect
- OpenID Connect Backchannel Authentication
- OpenID Connect Client Initiated Backchannel Authentication Flow
- OpenID Connect Federation Async
- OpenID Connect Flows
- OpenID Connect MODRNA Authentication Profile 1.0
- OpenID Connect Use Cases
- OpenID Connect for Identity Assurance
- OpenPDS
- Opportunistic encryption
- OxTrust
- PDC Emulator FSMO Role
- PKCS12
- PLAIN SASL Mechanism
- Pass-the-hash
- Pass-the-ticket
- Password
- Password Authentication
- Password Authentication Protocol
- Password Authentication is Broken
- Password Expiration
- Password Grace Authentication
- Password Management
- Password Synchronization
- Password Synchronization Lotus Notes
- Password Validator
- Passwordless Authentication
- Passwordless SMS Authentication
- Payment Card Industry Data Security Standard
- Payment Services Directive
- Perfect Forward Secrecy
- Permissioned Systems
- Ping Identity
- Point-to-Point Protocol
- Pre-Shared Key Ciphersuites for Transport Layer Security (TLS)
- Presentation Attack Detection
- Primary Refresh Token
- Privacy Considerations
- Privilege Management Infrastructure
- Prompt Parameter
- Proof of Ownership
- Proxy
- PseudoServer
- Public Key Infrastructure Weaknesses
- PwdEndTime
- PwdStartTime
- Quality of Protection
- REAL ID
- RFC 2831
- RFC 7235
- RFC 7253
- RSA key-exchange
- Registration
- Relationship
- Remote Authentication Dial-In User Service
- Replay attack
- Repudiation
- Resource Access Control Facility
- Risk Assessment
- Risk-Based Authentication
- SAML
- SAML Web Browser Profiles
- SASDFM
- SASL
- SASL Mechanisms
- SCIM
- SCIM 2.0
- SDA
- SNMP
- SPNEGO
- SSL Handshake Failed
- Samba
- Schannel SSP
- Secure Password Manager
- Security Assertion Markup Language (SAML) 2.0 Profile for OAuth 2.0 Client Authentication and Authorization Grants
- Security Controls For This Wiki
- Security Domain
- Security Information and Event Management
- Security Reference Monitor
- Security Support Provider
- Security Support Provider Interface
- Security Token
- Security-constraint
- Sender Policy Framework
- Serverless
- Service Ticket
- ServicePrincipalName
- Session Management
- Shared Secret
- Signature Verification
- Simple Authentication
- Single Logout
- Single Sign-On
- Single Sign-On Scenarios
- Social Login
- Socket Secure
- Something You Are
- Something You Have
- Something You Know
- State of the Internet-Security Report
- Strength of Function for Authenticators
- Subscriber Identification Module
- SupportedAuthPasswordSchemes
- Symmetric Key Cryptography
- System for Cross-domain Identity Management
- TLS Session Resumption
- Technical Positions Statements
- The SRP Authentication and Key Exchange System
- The Simple Public-Key GSS-API Mechanism
- ThisWilki
- Ticket Granting Service
- Time synchronization
- Tips using UnboundID LDAP SDK
- Token
- Touch ID
- Transparent Proxy
- Transport Layer Security
- Trust
- Trust Anchor Management Protocol
- Trust Framework Provider
- TrustedDomain
- Two-Factor Authentication
- U2F
- Unauthorized
- Unbind Request
- Universal Second Factor
- User-Managed Access
- UserInfo Request
- Using the Secure Remote Password (SRP) Protocol for TLS Authentication
- Vector of Trust Request
- Vectors of Trust
- Visitor Location Register
- Vulnerability
- W3C Credential Management API
- WEB Access Management
- WIKI-Roles
- WWW-Authenticate
- Web Authentication
- Web Authentication API
- WebAuthn Attestation
- WebAuthn Authentication
- WebAuthn Extension Identifiers
- WebAuthn Registration
- WebID
- WebSEAL
- What is missing in OAuth 2.0
- Why OAuth 2.0
- Why OpenID Connect
- Why Use Tokens
- Windows Authentication Package
- Windows Client Authentication Architecture
- Windows Credential Provider
- Windows Integrated Authentication
- Windows Logon
- Windows Logon Types
- Windows Server NT
- Windows.Security.Credentials.UI
- Winlogon
- X.500
- XDAS Resource Access
- Yadis
- Yubico
- Yubikey NEO
- [#1] - http://en.wikipedia.org/wiki/Authentication
 - Retrieved 2012-11-22
- Retrieved 2012-11-22
- [#2] - Gartner defines "user authentication"
